Multifactor Authentication (MFA)
Device Requirements
Eaton's Standard MFA factors require one at least one of the below
- Smart Phone and Tablet (either Eaton Managed or Personal)
- Android
- iOS
- Eaton Managed/Owned PC
- Windows
- Mac
Please Note
- The some mobile based Factors are not managed by Eaton.
- Google Authenticator and Microsoft Authenticator Apps
- Installed directly from a Public App Store (e.g. Google Play or Apple App Store)
- Okta Verify for Mobile
- Personal Devices: This app can be installed directly from a Public App Store (e.g. Google Play or Apple App Store)
- Eaton Managed Devices: This application is pushed automatically to Eaton Managed Devices
- Google Authenticator and Microsoft Authenticator Apps
- Personal devices:
- Eaton will not be able manage of your device with these applications
- Eaton can not see any data on your device
- The device is only used to receive a push notification or store an off-line token (Time-Based One Time Password) code.
- Use of a personal device is purely voluntary.
Eaton's Standard Factors
- Okta Verify (Recommended)
- Features a Push noticiation as the additional "Factor" allowing users to quickly authenticate
- Google Authenticator
- Provides Time-Based One Time Password (TOTP) which changes every 30-60 seconds
- Microsoft Authenticator
- Can be used instead of Google Authenticator
- KeePassXC
- A desktop password manager that provides Time-Based One Time Password (TOTP) which changes every 30-60 seconds
- Can be used instead of Google Authenticator
- Security Key or Biometric
- YubiKey
or Google Titian
- Hardware based authenticator
- Windows Hello on PC
- Important Note: Not currently supported by Zscaler, but can be used with other Okta protect applications
- TouchID, or FaceID on Mobile
- YubiKey
or Google Titian
Setup MFA
There are two ways to setup MFA. When prompted during login if it is your first time logging into an Okta Protected application or via account settings.
Important Considerations
- Having multiple factors active ensures that you can self manage your EID Account including MFA Factors.
- Any combo of factors is better than just one for.
- Okta Verify Desktop + Okta Verify Mobile
- Okta Verify Desktop + Okta Verify Mobile + Google Authenticator
- Okta Verify Mobile + Microsoft Authenticator
- Any combo of factors is better than just one for.
- You can set up Multiple Okta Verify factors on different devices
- Okta Verify on Desktop (Windows, Mac)
- Okta Verify on Mobile (iOS, Android, iPad)
Device Replacement Recommendations
- Set up multiple factors so you have a backup in the event of an emergency.
- If you know you're replacing your existing device DO NOT wipe your old device before enrolling your new device as a factor
During Login
If you do not have an MFA factor enrolled and you attempt to access an Okta Protected application, you will be prompted to enroll in a required factor.
- During initial logon, A choice of factors will be presented.
-
Choose a factor and click "setup" for guided instructions on how to setup the factor selected

User Account Settings
If you'd like to add addtional or modify your current MFA factors, you can do so from the eid.eaton.com Okta Dashboard User Settings Page.
- Logon to eid.eaton.com
-
At the top right-hand side of the page, click your name
-
From the drop down click "Settings"
-
Click "Edit Profile"

-
Confirm your indentity by following the prompts.

-
Find the "Security Methods" section and select which factor you'd like to change/remove

Detailed Steps on Factor Setup
For a detailed walk through of each factor set up please refer to the below. Please note, some screenshots may contain older versions of application screens.
Okta Verify for Mobile
Reference
- Ensure that "Okta Verify" is installed on your iOS device
- On an Eaton Managed Device, you should download it from the Eaton Managed App Store
- On a Personal Device, you can download it from the Apple App Store or Google Play Store.
- Open the Okta Verify Application on your Mobile Device
-
Click + to add an account

-
Select Organization as the Account Type

-
Click "Skip" when prompted "Add Account from another Device"

-
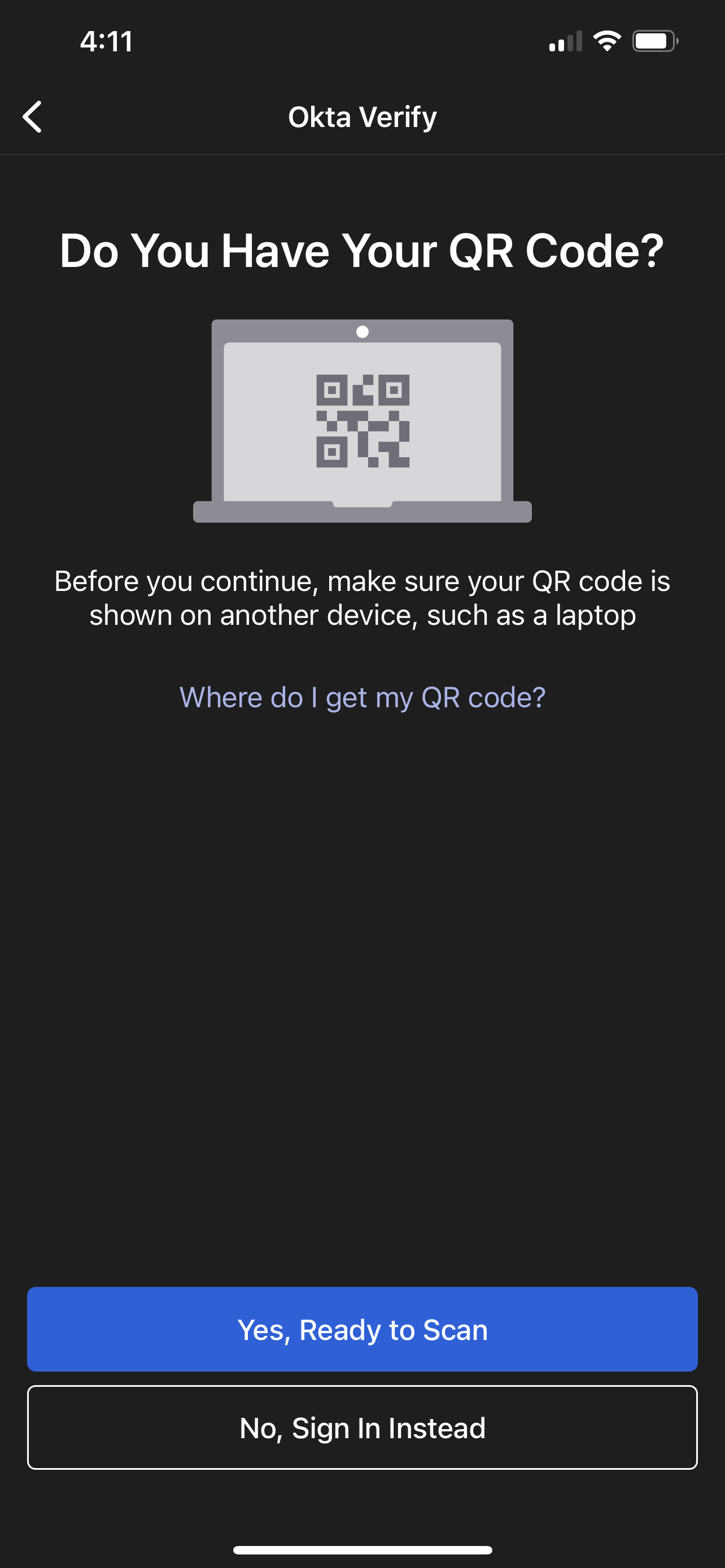
Click "No, Sign in Instead" when prompted for a QR code
-
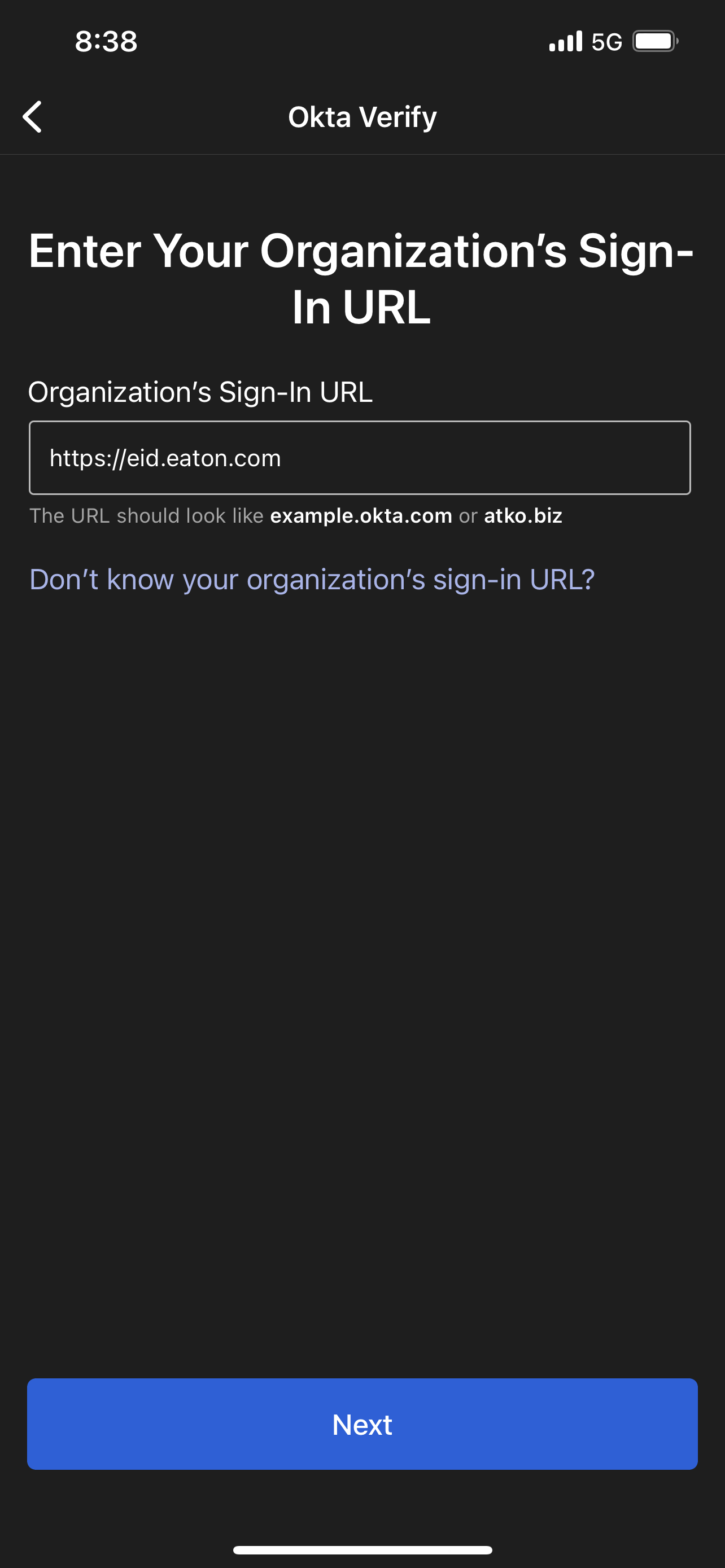
If not automatically populated, enter https://eid.eaton.com in the Sign on URL field
-
Follow the Sign in prompts, entering your UserName and Password
-
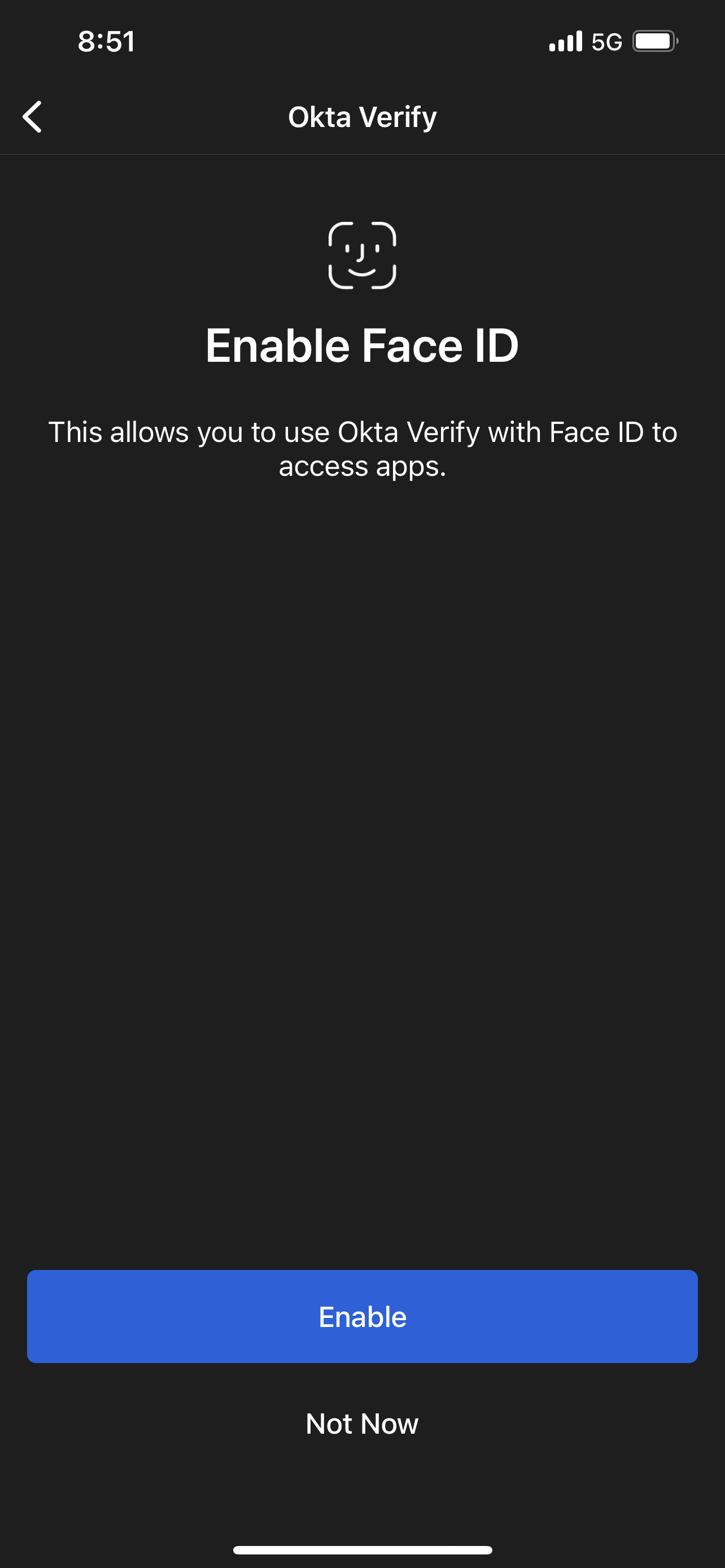
OPTIONAL: Enable Biometerics
Tip
Enabling FaceID or TouchID on your device will allow you to easily transfer your Okta Verify set up to a new device in the future, but it is not required for normal use.
-
Once you've signed in completely, you will recieve a confirmation that your account was added
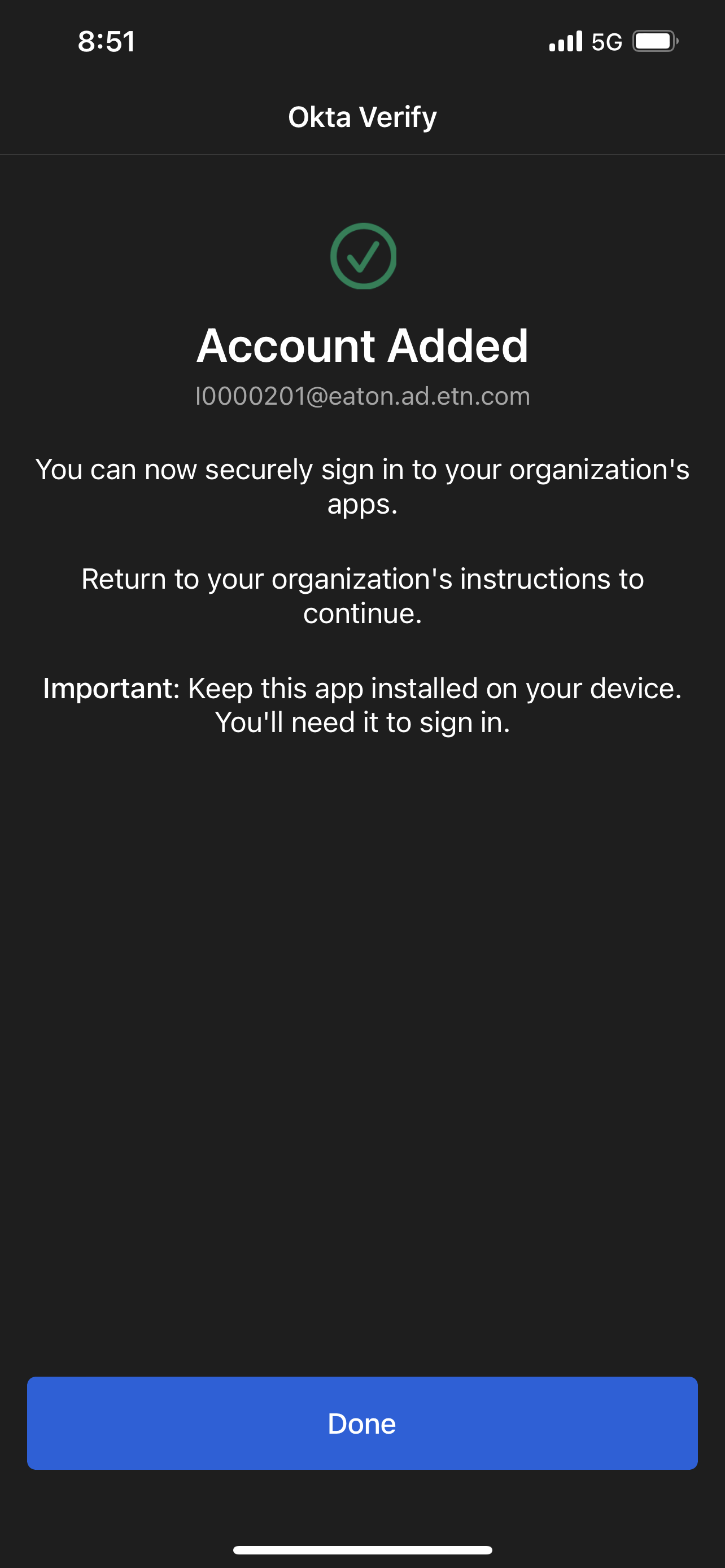
Okta Verify for Desktop
- Confirm you have Okta Verify for Desktop installed on your PC.
- Open the Okta Verify application on your PC.
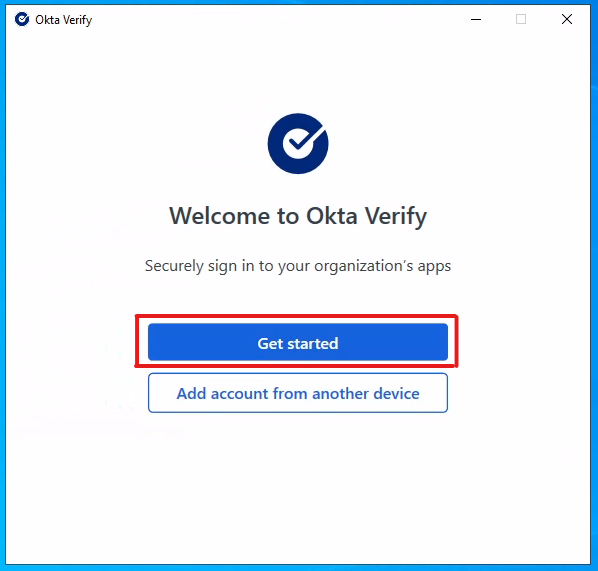
-
Click "Get started"
-
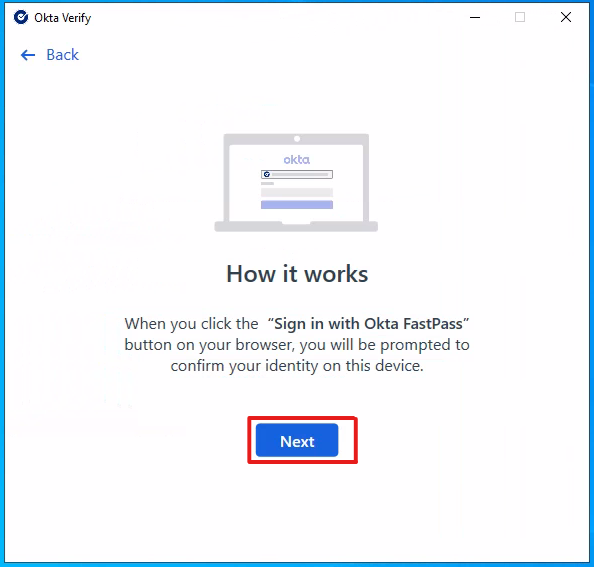
Click Next
-
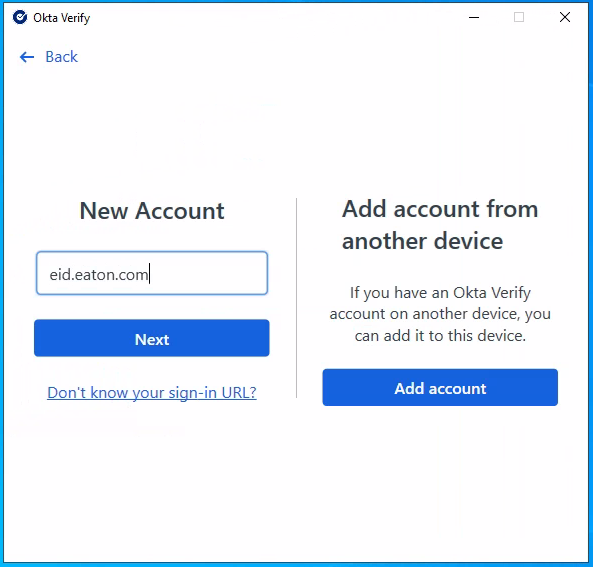
If not already populated enter https://eid.eaton.com in the sign-in URL field.
-
Your default Web Browser will open and direct you to the eid.eaton.com login page. Follow all sigin prompts and any MFA challenges.
-
Once you've signed in you will recieve a notification that Your identity has been verified and you'll be routed back to the Okta Verify Desktop application.
-
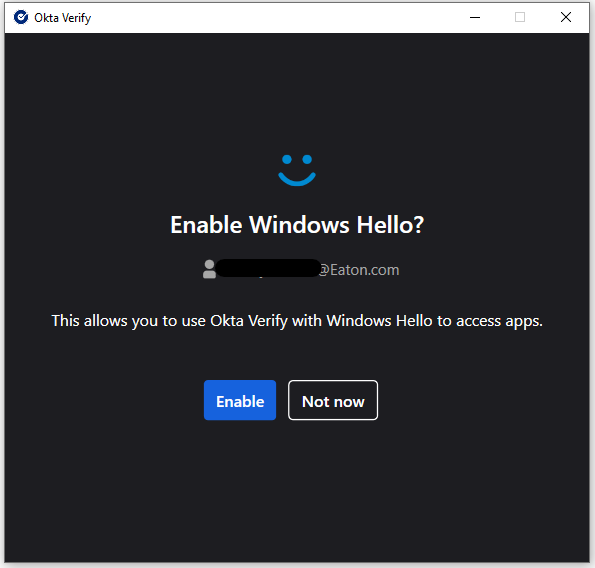
OPTIONAL: If you have Windows Hello on your PC, the Okta Verify Application will ask if you'd like to Enable Windows Hello. This is not required for normal use.
-
You'll see a confirmation that your account has been added.
Google Authenticator
- On your Desktop, when prompted to set up MFA. Click Setup next to Google Authenticator
-
Download Google Authenticator on your Mobile Device from the App Store
-
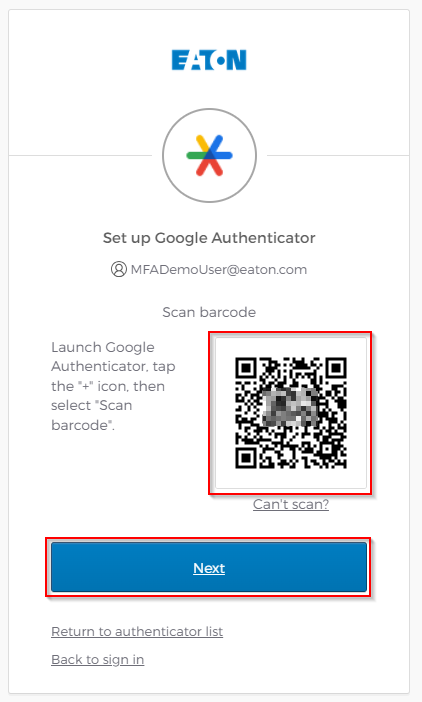
Using the Google Authenticator App, Scan the QR Code
DO NOT scan the code from this help document. Each QR Code is unique to your account alone.
-
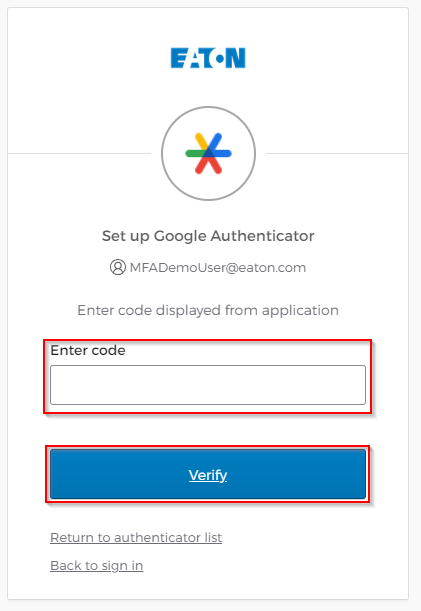
Enter the code from Google Authenticator and click verify
Microsoft Authenticator
The Microsoft Authenticator app can be used in place of Google Authenticator. Only one "Authenticator App" can be setup on yoiur at a time.
Okta will to refer to this factor as Google Authenticator
- On your Desktop, when prompted to set up MFA, Click Setup next to Google Authenticator
-
Open the Microsoft Authenticator App, tap the "+" icon, then

-
Tap "Other (Google, Facebook, etc.)"
-
Scan the QR code.
DO NOT scan the code from this help document. Each QR Code is unique to your account alone.

-
Click next
-
Enter the code from Microsoft Authenticator and click verify

Special Exception Factors
SMS
This Factor will send a code to an SMS enabled mobile phone. The code can then be entered into the eid.eaton.com login prompt.
An exception can be requested to use SMS as a Factor with your EID (Okta) account. SMS is considered a weak factor and can only be used when the standard factors will not work. This request should only be made if the Standard Factors cannot be used. This exception requires approval from your manager due to the potential risk.
IMPORTANT:
The exception for this factor will be revoked when access to high risk applications is granted. At the time of assignment the SMS Factor will no longer work for a user for any application.